
The DCW Research DORA Part 2
Includes: Abbreviations, Terms, Definitions, Official Websites, and a Planning and Implementation Guide
Date: January 22nd, 2026
Prepared by: Eric Williamson, Director of Compliance and Risk
Classification: Industry Analysis - Public
Executive Summary
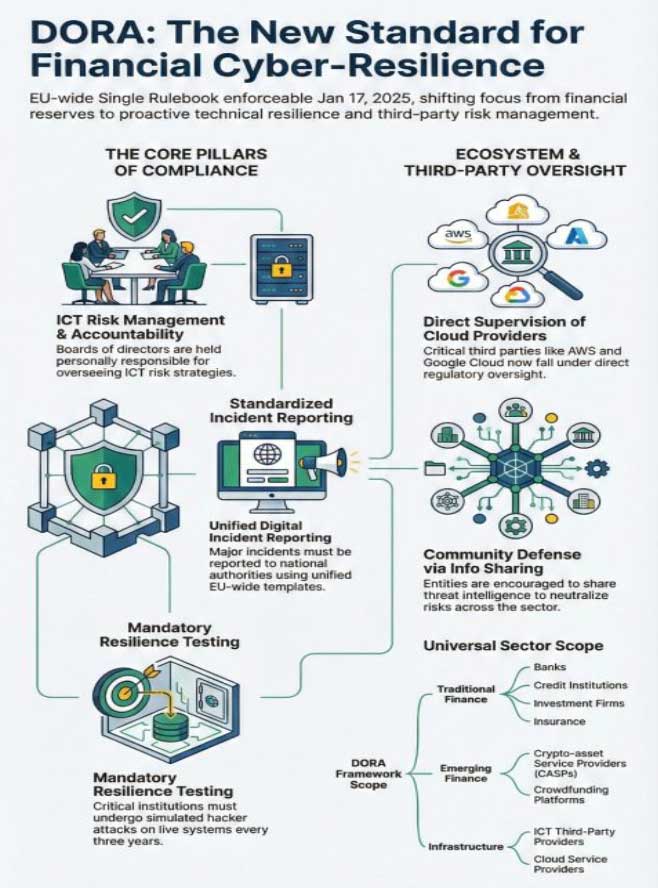
The Digital Operational Resilience Act, known throughout the financial services industry as DORA, represents a watershed moment in European financial regulation. Fully applicable as of January 17, 2025, it fundamentally transforms how financial institutions across the European Union must approach information and communication technology (ICT) risk management, operational continuity, and digital resilience.
For the first time, the European Union has established a harmonised, detailed, and enforceable regulatory framework that addresses technology risks with the same rigour traditionally reserved for financial risks such as capital adequacy and market conduct. DORA emerged from a recognition that the financial sector's increasing dependence on digital technology has created new vulnerabilities that traditional regulatory frameworks were not designed to address.
The Five Pillars
The regulation establishes five interconnected pillars that collectively define what digital operational resilience means in practice:
- ICT Risk Management: The foundational framework for identifying and controlling technology risks.
- Incident Management and Reporting: Ensuring rapid response when disruptions occur.
- Digital Operational Resilience Testing: Validating that systems and processes work as intended under stress.
- Third-Party Risk Management: Addressing the growing dependence on external technology providers.
- Information Sharing: Fostering collective defence against common cyber threats.
Application and Scope
What makes DORA particularly significant is its breadth of application and its unprecedented level of detail. The regulation applies directly to more than twenty thousand financial entities across the European Union. Importantly, DORA also extends regulatory requirements to information and communication technology service providers that support these financial entities, particularly cloud computing platforms, software vendors, and data centre operators.
Abbreviations
| Abbreviation | Term |
|---|---|
| BCP / DRP | Business Continuity Plan / Disaster Recovery Plan |
| BIA | Business Impact Analysis |
| CA / NCA | Competent Authority / National Competent Authorities |
| CDR / CIR | Commission Delegated Regulation / Commission Implementing Regulation |
| CIF | Critical or Important Function |
| CSIRT | Computer Security Incident Response Team |
| CTTP | Critical ICT Third-Party Service Provider |
| CySA | Cybersecurity Act, Regulation (EU) 2019/881 |
| DORA | Digital Operational Resilience Act, Regulation (EU) 2022/2554 |
| DORS | Digital Operational Resilience Strategy |
| DORT | Digital Operational Resilience Testing |
| ENISA | European Union Agency on Cybersecurity |
| ESAs | European Supervisory Authorities (EBA, EIOPA, ESMA) |
| FE | Financial Entity |
| IAF | Internal Audit Function |
| ICT | Information and Communication Technology |
| ICT RMF | ICT Risk Management Framework |
| ICT TPP / TPSP | ICT Third-Party Service Provider / Third-Party Service Providers |
| IGCF | Internal Governance and Control Framework |
| ISMS | Information Security Management System |
| KRI / KCI / KPI | Key Risk / Control / Performance Indicator |
| NIS 2 | NIS 2 Directive, Directive (EU) 2022/2555 |
| RCA | Root Cause Analysis |
| RoI | Register of Information (DORA Art.28.3) |
| RTO / RPO | Recovery Time Objective / Recovery Point Objective |
| RTP | Risk Treatment Plans |
| SLAs / OLAs | Service Level Agreements / Operational Level Agreements |
| SoA | Statement of Applicability |
| TI | Threat Intelligence |
| TLPT | Threat-Led Penetration Testing |
| TPRM | Third-Party Risk Management |
Terms and Definitions
| Term | Definition | Source |
|---|---|---|
| Digital operational resilience | The ability of a financial entity to build, assure and review its operational integrity and reliability by ensuring, either directly or indirectly through the use of services provided by ICT third-party service providers, the full range of ICT-related capabilities needed to address the security of the network and information systems which a financial entity uses, and which support the continued provision of financial services and their quality, including throughout disruptions. | DORA |
| ICT risk management framework | The ICT risk management framework is part of financial entities' overall risk management system, enabling them to address ICT risk quickly, efficiently, and comprehensively and to ensure a high level of digital operational resilience. It shall include at least strategies, policies, procedures, ICT protocols and tools that are necessary to duly and adequately protect all information assets and ICT assets. | DORA Art.6 |
| Critical function | A function, the disruption of which would materially impair the financial performance of a financial entity, or the soundness or continuity of its services and activities, or the discontinued, defective or failed performance of that function would materially impair the continuing compliance of a financial entity with the conditions and obligations of its authorisation, or with its other obligations under applicable financial services law. | DORA |
| Legacy ICT system | An ICT system that has reached the end of its lifecycle (end-of-life), that is not suitable for upgrades or fixes, for technological or commercial reasons, or is no longer supported by its supplier or by an ICT third-party service provider, but that is still in use and supports the functions of the financial entity. | DORA |
| ICT concentration risk | An exposure to individual or multiple related critical ICT third-party service providers creating a degree of dependency on such providers so that the unavailability, failure or other type of shortfall of such provider may potentially endanger the ability of a financial entity to deliver critical functions, or cause it to suffer other types of adverse effects, including large losses, or endanger the financial stability of the Union as a whole. | DORA |
| Major ICT-related incident | An ICT-related incident that has a high adverse impact on the network and information systems that support critical or important functions of the financial entity. | DORA |
| Threat-led penetration testing (TLPT) | A framework that mimics the tactics, techniques and procedures of real-life threat actors perceived as posing a genuine cyber threat, delivering a controlled, bespoke, intelligence-led (red team) test of the financial entity’s critical live production systems. | DORA |
Relevant Regulations (CDRs & CIRs)
The following Commission Delegated Regulations (CDRs) and Implementing Regulations (CIRs) supplement DORA:
- CDR (EU) 2025/532: Regulatory technical standards specifying the elements that a financial entity has to determine and assess when subcontracting ICT services supporting critical or important functions.
- CDR (EU) 2025/1190: Regulatory technical standards specifying the criteria used for identifying financial entities required to perform threat-led penetration testing (TLPT).
- CDR (EU) 2025/420: Regulatory technical standards specifying the criteria for determining the composition of the joint examination team.
- CIR (EU) 2025/302: Implementing technical standards for the application of Regulation (EU) 2022/2554 with regard to standard forms, templates, and procedures for financial entities to report a major ICT-related incident.
- CDR (EU) 2025/301: Regulatory technical standards specifying the content and time limits for the initial notification of, and intermediate and final report on, major ICT-related incidents.
- CIR (EU) 2024/2956: Implementing technical standards for the application of Regulation (EU) 2022/2554 with regard to standard templates for the register of information.
- CDR (EU) 2024/1774: Regulatory technical standards specifying ICT risk management tools, methods, processes, and policies and the simplified ICT risk management framework.
Planning and Implementation
Maturity Levels
| Level | Definition & Criteria |
|---|---|
| 0. Non-existent | No attention has been paid to this control measure. No or limited control measures implemented. |
| 1. Initial | The control measure is (partially) defined, but is implemented inconsistently. There is a great deal of dependence on individuals. |
| 2. Repeatable but informal | The control measure is in place and implemented in a consistent, structured, but informal manner. There is limited evidence of design and existence. |
| 3. Defined | The design of the control measure is documented and implemented in a structured and formalised manner. The required effectiveness of the control measure is demonstrable and is tested. |
| 4. Effective and measurable | In addition to the effectiveness of individual control measures, the effectiveness of the coherence of all information security measures is also periodically evaluated. |
| 5. Continuous improvement | Continuous efforts are made to improve the effectiveness of the system of control measures by taking future risks into account. |
RACI Chart (Roles and Responsibilities)
R: Responsible, A: Accountable, C: Consulted, I: Informed
| Topic | Mgmt Board | Legal / Comp | Risk / TPRM | Internal Audit | Procurement | Cyber | IT / ICT | BCP | HR | DPO |
|---|---|---|---|---|---|---|---|---|---|---|
| 0. DORA project mgmt | A | R | C | C | I | C | C | C | I | I |
| 1. Governance & Oversight | A | R | R | R | - | C | C | C | C | - |
| 2. ICT/DORA Strategies | A | C | C | I | - | R | R | R | I | - |
| 3. Asset inventory | A | C | C | - | C | R | R | R | - | C |
| 4. ICT risk management | A | C | R | - | - | R | R | I | - | - |
| 5. ISMS | A | C | I | - | - | R | R | I | C | I |
| 6. ICT operations | A | - | - | - | - | C | R | I | - | I |
| 7. Incident management | A | R | I | - | - | R | R | I | - | R |
| 8. BCP & Crisis Mgmt | A | R | I | I | - | R | R | R | R | I |
| 9. Contract mgmt / RoI | A | R | C | - | R | C | C | C | - | C |
| 10. TPRM | A | R | R | I | R | R | C | I | - | R |
| 11. Testing (TLPT) | A | I | I | I | C | R | R | R | - | I |
| 12. Info-sharing | A | C | I | - | - | R | - | I | - | I |
Comprehensive DORA Implementation Checklist
1. General
| x | Topic | Tasks | Reference |
|---|---|---|---|
| ☐ | 1.1. Requirements and Guidelines | Collect and study all DORA-related requirements (including Commission Delegated Regulation), ESAs’ and local authorities’ Technical Standards, Guidelines & Recommendations. Make and regularly review a list of them. | DORA, CDRs/CIRs |
| ☐ | 1.2. DORA Scope | Determine the boundaries and applicability of the DORA to establish its scope. Check the references in Article 16, “Simplified ICT risk management framework”. | DORA: art.2, 16.1 |
| ☐ | 1.3. Proportionality principle | Identify internal and external factors affecting digital operational resilience, including company size and overall risk profile, as well as the nature, scale, and complexity of services. | DORA: art.4 |
| ☐ | 1.4. Introductory meeting | Organise an introductory meeting with the Management Body. Make sure that the Management Body is fully supportive and committed. | DORA: art.5.2a, 5.2g, 5.4 |
| ☐ | 1.5. Implementation team | Gather an implementation team. Create and, if necessary, approve a DORA implementation plan and project charter. Conduct a kick-off meeting. | DORA: art.5.2g |
| ☐ | 1.6. Document Management | Define the requirements for managing DORA-related documentation and prepare appropriate templates. Create and maintain a register for DORA-related documents. | DORA: art.6.1, 8.1 |
2. Internal Governance and Control Framework (IGCF)
| x | Topic | Tasks | Reference |
|---|---|---|---|
| ☐ | 2.1. Gap Analysis | Conduct a Gap analysis to understand the current state of the IGCF. | Guidelines (GIG) |
| ☐ | 2.2. Management body | Describe (review) the information on the structure, organisation, members and responsibilities of the management body. | DORA: art.5.2a,c |
| ☐ | 2.3. Committees | Establish a Risk committee, Audit committee and other necessary committees (e.g., Cybersecurity, Business Continuity, Privacy). | GIG |
| ☐ | 2.6. Risk management function | Design and implement (review) a Risk Management Function (RMF). | DORA: art.6.4 |
| ☐ | 2.8. Internal audit function | Design and implement (review) an Internal Audit Function (IAF). Plan, establish, implement, and maintain an audit program to evaluate the effectiveness of the ICT RMF. | DORA: art.6.4, 6.6 |
| ☐ | 2.11. Business continuity function | Design and implement a Business continuity function (BCF). | GIG |
| ☐ | 2.12. Executive training | Conduct regular training for the management body to improve knowledge and skills in understanding ICT risks. | DORA: art.5.4 |
3. ICT Risk Management Framework (ICT RMF)
| x | Topic | Tasks | Reference |
|---|---|---|---|
| ☐ | 3.1. Gap Analysis (ICT RMF) | Conduct a Gap analysis to understand the current state of the ICT RMF. | CDR 2024/1774 |
| ☐ | 3.3. Digital operational resilience strategy | Plan and Design the ICT RMF. Establish a Digital operational resilience strategy, align it with the ICT strategy. | DORA: art.5.2d, 6.8 |
| ☐ | 3.7. Asset inventory | Identify, classify and adequately document all ICT-supported business functions, the information assets and ICT assets supporting those functions. Annually review. | DORA: art.8.1, 8.4 |
| ☐ | 3.9. ICT Risk Assessment | Conduct ICT Risk identification and assessment. | DORA: art.8.2, 8.3 |
| ☐ | 3.10. Legacy ICT systems | Annually conduct a specific ICT risk assessment on all legacy ICT systems. | DORA: art.8.7 |
| ☐ | 3.11. ICT security | Design, procure and implement ICT security policies, procedures, protocols and tools. Document a Statement of Applicability (SoA) if needed. | DORA: art.7, 9.2 |
| ☐ | 3.13. Monitoring | Implement mechanisms to promptly detect anomalous activities, including ICT network performance issues and ICT-related incidents. | DORA: art.10 |
| ☐ | 3.14. ICT business continuity policy | Establish an ICT business continuity policy. Determine recovery time and recovery point objectives (RTO/RPO). | DORA: art.11.1 |
| ☐ | 3.19. Backup and recovery | Develop and document backup and recovery policies and procedures. Regularly review and test them. | DORA: art.12.1-12.3 |
| ☐ | 3.21. Threat intelligence | Have in place capabilities and staff to gather information on vulnerabilities and cyber threats. | DORA: art.13.1 |
4. Incident Management and Reporting
| x | Topic | Tasks | Reference |
|---|---|---|---|
| ☐ | 4.1. Incident management process | Define, establish and implement an ICT-related incident management process, including root causes analysis and post incident review. | DORA: art.17.1, 18.1 |
| ☐ | 4.2. Incident notification | Define, establish and implement a process to report major ICT-related incidents to the relevant competent authority and affected client. | DORA: art.19.1 |
| ☐ | 4.3. Annual costs and losses | Be ready to report to the competent authorities, upon their request, an estimation of aggregated annual costs and losses caused by major ICT-related incidents. | DORA: art.11.10 |
5. Digital Operational Resilience Testing (DORT)
| x | Topic | Tasks | Reference |
|---|---|---|---|
| ☐ | 5.1. DORT programme | Establish and maintain a digital operational resilience testing programme. | DORA: art.24.1 |
| ☐ | 5.2. Annual tests | Annually conduct appropriate tests of all ICT systems and applications supporting critical or important functions. | DORA: art.24.6 |
| ☐ | 5.3. Vulnerability assessments | Conduct vulnerability assessments before any deployment or redeployment of new or existing applications and infrastructure components. | DORA: art.25.2 |
| ☐ | 5.4. Threat-led penetration test (TLPT) | Conduct regular (at least every 3 years) threat-led penetration tests. Get an attestation confirming that the test was performed. | DORA: art.26-27 |
6. ICT Third-Party Risk Management (TPRM)
| x | Topic | Tasks | Reference |
|---|---|---|---|
| ☐ | 6.1. TPRM Strategy and Policy | Establish a Strategy on ICT third-party risk, including a Policy on the use of ICT services supporting critical or important functions. | DORA: art.28.1 |
| ☐ | 6.3. Register of contractual arrangements | Fill in and maintain a register of contractual arrangements on the use of ICT services provided by ICT third-party service providers. | DORA: art.28.3 |
| ☐ | 6.6. Exit strategies | Prepare exit strategies for ICT services supporting critical or important function. | DORA: art.28.8 |
| ☐ | 6.7. Due Diligence | Integrate an extended Due Diligence procedure into the purchasing process. Identify and assess risks. | DORA: art.28.4 |
IMPORTANT NOTICES
Disclaimer: The content provided in this article is for general informational and educational purposes only. This information is not intended to be considered legal, financial, medical, or professional advice. By accessing and using this article, you acknowledge and agree that no professional relationship or duty of care is established between you and the authors, owners, or operators. The information presented may not be current, complete, or applicable to your specific circumstances. It should not be relied upon as a substitute for seeking advice from qualified professionals in relevant fields. The authors, owners, and operators are not liable for any losses, damages, or adverse consequences resulting from your use of or reliance on the content.
Accuracy and Currency: While we endeavour to ensure accuracy, the information provided may not be current, complete, or applicable to your specific circumstances. Security threats and regulatory requirements evolve rapidly. You should conduct your own research and seek professional advice before taking any action based on this information.
EAJW © 2026 DCW Research. All rights reserved













